Lazarus is a hacking group believed to be from North Korea.
According to a report from security firm Kaspersky, the group is improvising their strategies by taking “more careful steps” and by employing “improved tactics and procedures” to spread malware and steal cryptocurrencies from potential victims.
In other words, Lazarus has adjusted the way it infects a system, remains undetected, and illicitly obtains cryptocurrency from compromised machines and victims.
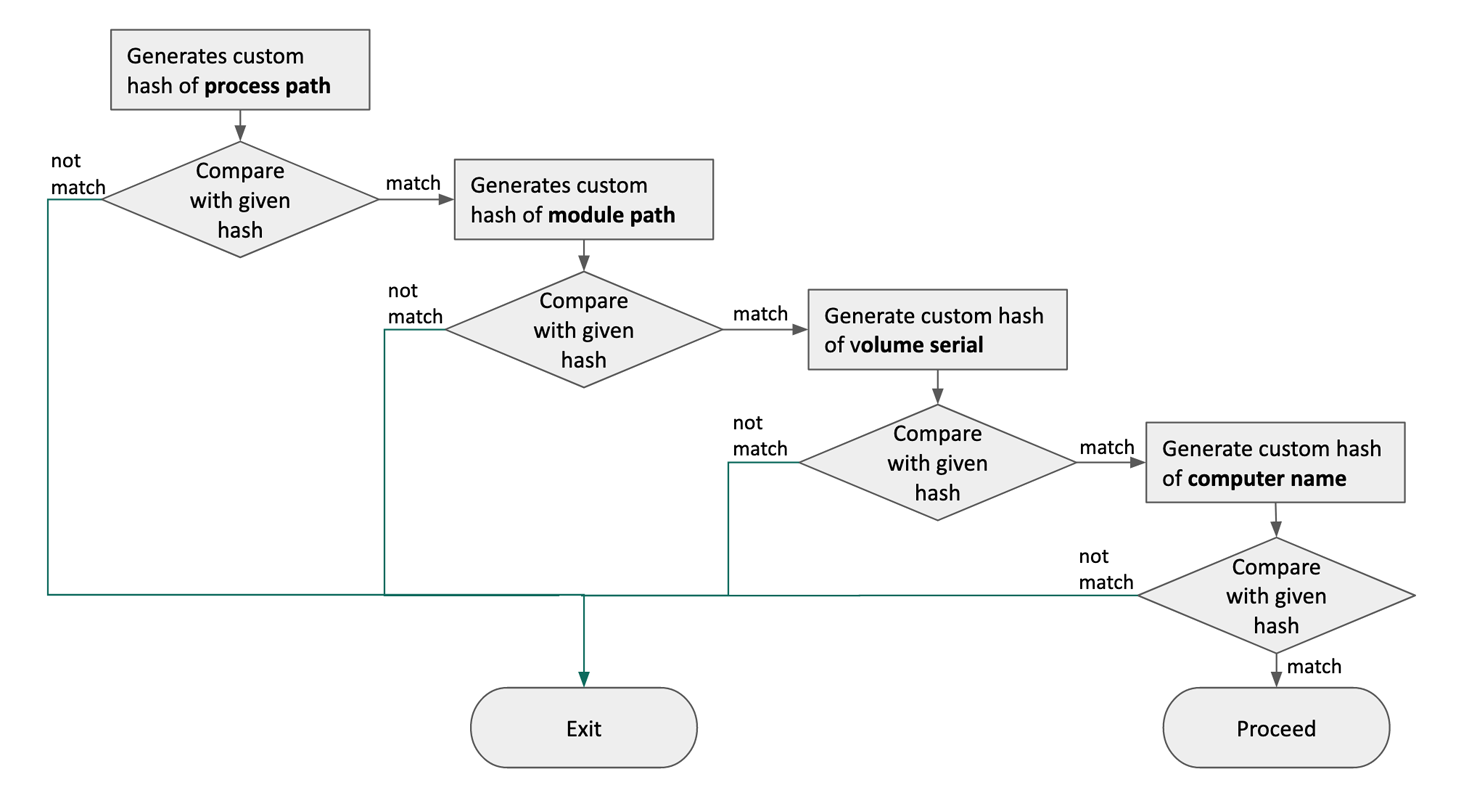
First, according to Kaspersky, is Lazarus in executing it malware inside the victims devices memory rather than being run from hard disk drives. And second, the researchers said that the hacking group is using the messaging app Telegram as one of its attack vectors.
The security researchers dubbed this wave of tactics as 'Operation AppleJeus Sequel', the evolution of the 'AppleJeus' campaign that was uncovered back in 2018 and ran throughout 2019.

Just like AppleJeus, AppleJeus Sequel also use fake cryptocurrency trading companies to lure in victims. The fake companies have websites complete with links, and fake Telegram trading groups.
Lazarus use Telegram to spread the malware, which would then be downloaded by victims through the app. When the malware infects its victims, the operating system is compromised by a malicious payload. This way, attackers can gain remote access to control the compromised device and further their attacks. Lazarus almost always goes after cryptocurrency.
Telegram itself wasn’t compromised.
"Based on these, we assess with high confidence that the actor delivered the manipulated installer using the Telegram messenger. Unfortunately, we can’t get all the related files as some payloads were only executed in memory. However, we can reassemble the whole infection procedure based on our telemetry. The overall infection procedure was very similar to the WFCWallet case, but with an added injection procedure, and they only used the final backdoor payload instead of using a tunneling tool," said the researchers.
During its research, Kaspersky found a number of these fake cryptocurrency trading websites, and mentioned that it has identified several victims from the UK, Poland, Russia, and China.
Several of these victims were confirmed to be in the cryptocurrency business.
While the amount of cryptocurrency or other funds Lazarus managed to obtain through this campaign wasn’t mentioned, a UN report published in August 2019, suggested that the North Korean hackers were thought to have stolen at least $2 billion by hacking foreign financial institutions and cryptocurrency exchanges.
"Since the initial appearance of Operation AppleJeus, we can see that over time the authors have changed their modus operandi considerably. We assume this kind of attack on cryptocurrency businesses will continue and become more sophisticated."