
Meta operates a vast empire of social media platforms, and for convenience, everything can be controlled using one single account.
And that is managed through Meta's centralized login system, a versatile and extremely easy login system for users to use. The things is however, a critical bug was found in the system, which could have allowed malicious actors to bypass account's two-factor authentication (2FA) protection just by knowing their email address or phone number.
The bug was discovered by Gtm Mänôz, a security researcher from Nepal.
He realized that Meta did not set up a limit of attempts when a user entered the 2FA code used to log into their accounts on the updated Meta Accounts Center, which helps users link all of their Meta accounts, such as Facebook and Instagram, into one.
What this means, if hackers known a target's phone number or email address, they can simply enter the target's data, and link that number to a Facebook account their control.
The critical bug here is that, without upper limit to 2FA code tries someone could make, hackers could brute force to find the code without restriction.
And once malicious actors got the 2FA code right, the target's phone number will be automatically linked to the Facebook account the actors control.
From here, the attackers could simply launch a phishing attack to the target, given that that target no longer has two-factor authentication enabled anymore.
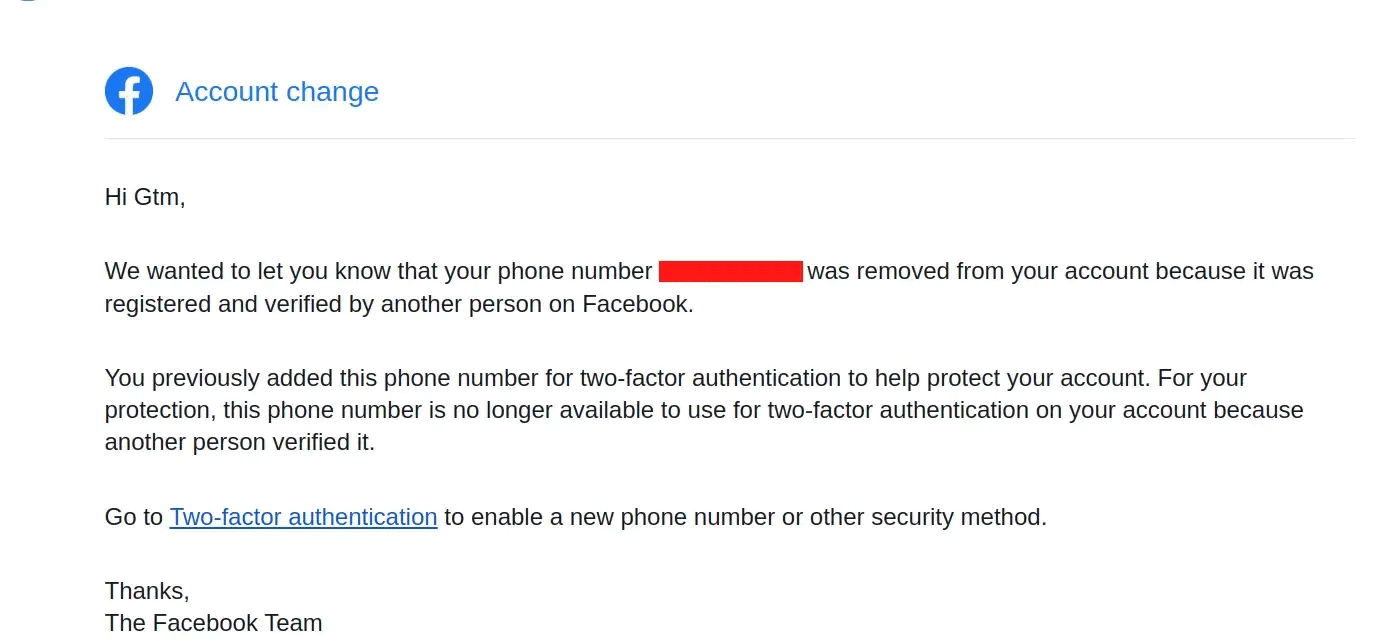
"If the phone number was fully confirmed and 2FA enabled in facebook, then the 2FA will be turned off or disabled from victim’s account," Mänôz explained. "And, if the phone number was partially confirmed that means only used for 2FA, it will revoke the 2FA and also the phone number will be removed from victim’s account."
"Basically the highest impact here was revoking anyone’s SMS-based 2FA just knowing the phone number," added Mänôz in an interview.
According to Mänôz in a blog post, he found the bug in the Meta Accounts Center in 2022, and reported it to the company in mid-September.
Meta fixed the bug a month later, and rewarded Mänôz $27,200 for reporting the bug.
While the bug has been patched, Meta didn't provide any details regarding the bug, and whether or not it has been exploited before it was fixed.
In a news post, Facebook only said that: