Cryptocurrency wallets' addresses are made of long strings of characters. One of the reasons is to make sure that people copy and paste the addresses to prevent typo.
But malicious actors have managed to take advantage of this fact, and found a way to steal cryptocurrencies from users by using a malicious apps that pose as "clipper" apps.
One of which, was the MetaMask app, discovered by by security researchers at ESET
When users copy a cryptocurrency wallet's long string of random characters, the users' device will store that address inside its clipboard. When this clipper app is installed, it will recognize the copied content as a cryptocurrency wallet's address, and intercepts the content to then replaces it with what the attacker wants to subvert.
In this case, it can be a wallet belonging to one the attacker.
According to ESET this is the first time a cryptocurrency malware of this type is found on the Play Store.
This dangerous kind malware was first discovered in 2017 on the Windows platform, and was then found hosted on third-party Android app stores in the summer of 2018.
The clipper apps' source codes were sold on underground hacking forums and since then, this malware has been detected in several shady app stores.
Then it was "In February 2019, we discovered a malicious clipper on Google Play, the official Android app store," ESET explained.
The researchers even discovered one hosted on download.cnet.com, a software-hosting website that considered as one of the most popular in the world.
Its primary targets are users who want to use the mobile version of the MetaMask service, which is designed to run Ethereum decentralized apps in a browser, without having to run a full Ethereum node.
The problem is, the service doesn't offer a mobile app, as it only has add-ons for desktop browsers such as Chrome and Firefox.
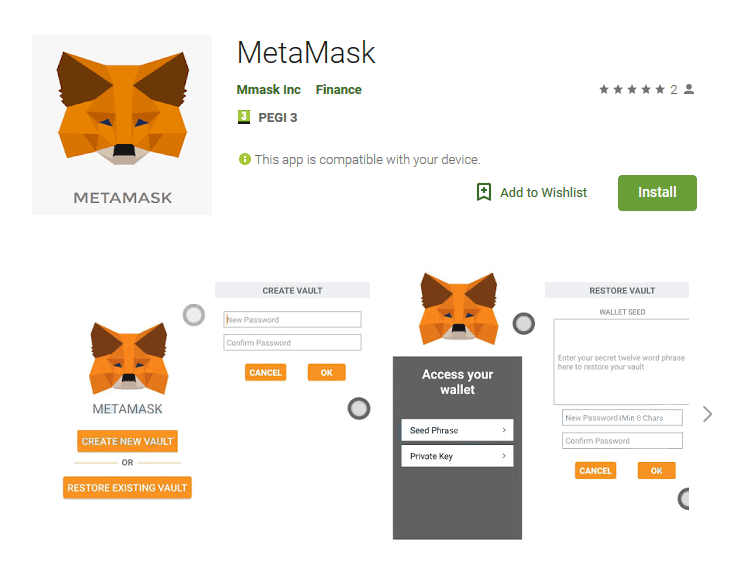
Clipper apps with malicious deeds are known as Android/Clipper.C.
Besides replacing cryptocurrency wallet addresses copied to the clipboard with one belonging to the attacker, the malware’s main purpose is to also steal victims' credentials and private keys to gain control over the victims' cryptocurrencies.
"We spotted Android/Clipper.C shortly after it had been introduced at the official Android store, which was on February 1, 2019. We reported the discovery to the Google Play security team, who removed the app from the Store," the report said.
Previously, several other malicious apps impersonating MetaMask have also been caught on Google Play . However, they merely phished for sensitive information with the goal of accessing the victims’ cryptocurrency funds.
As this is the first clipper app to have sneaked inside Google Play, there could be more in the future. For this reason, ESET suggested a few best practices for Android users to stick with for mobile security:
- Keep Android devices updated and always use reliable mobile security solution.
- Always install apps from Google Play Store.
- Always check on the official website of an app or service provider for the link to the official app. If there is none, proceed with extreme caution.
- Double-check every step in all transactions that involve anything valuable, from sensitive information to money. When using the clipboard, always check if the pasted content is not altered.