Software are merely products with flaws waiting to be exploited or patched.
Google and Microsoft are two of the largest technology companies in the world. Even with their immense resources and manpower, their products, can have bugs because their developers are humans, and humans are imperfect beings.
According to Google engineers, roughly 70% of all serious security bugs in the Chrome codebase are memory management and safety bugs.
The percentage was compiled after the Google engineers analyzed 912 security bugs they fixed in the Chrome stable branch since 2015, which had a "high" or "critical" severity rating.
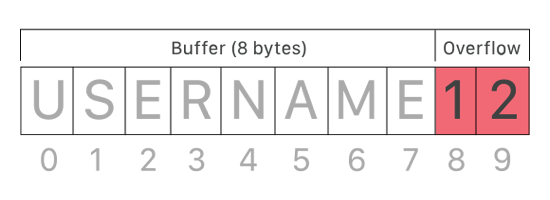
Memory safety is a term to describe applications that access the operating system's memory in a way that doesn't cause errors. And memory safety bugs happen when a software, accidentally or intentionally, accesses system memory in a way that exceeds its allocated size and memory addresses.
This kind of issue include terms like buffer overflow, race condition, page fault, null pointer, stack exhaustion, heap exhaustion/corruption, use after free, or double free.
These memory management vulnerabilities are the most sought-after bugs that attackers try to find, as exploiting them can give hackers the ability to plant code inside a device's memory and have it executed by the victim application.
70% is a number identical to what was shared by Microsoft.
Speaking at a security conference back in February 2019, Microsoft engineers said that for the past 12 years, around 70% of all the vulnerabilities in its products that have been addressed through a security update each year, are memory safety issues.
In Microsoft's case, by the time the company patched most of the basic memory safety bugs, hackers and bug hunters have also stepped up their game, moving away from basic memory errors to more complex exploits that run code at desired memory addresses.
This kind of exploit is ideal for targeting others apps and processes running on the system.
Memory safety errors are one of the biggest attack surfaces for hackers, and attackers seem to be capitalizing on their availability. According to Microsoft security engineer Matt Miller, use after free and heap corruption vulnerabilities continue to be the preferred bugs when attackers are developing exploits.
As software engineering has advanced tremendously over the years with developers getting better and better at addressing most security flaws by adding security protections in place, unfortunately, memory management vulnerabilities continue to be one of the most troublesome and persistent.
The reason for this high percentage is because both Google and Microsoft are basically dealing with the same problem: using C and C++, the two predominant but now considered "unsafe" programming languages in their codebases.
The two programming languages are old tools created decades ago, at the time when security exploitation and cyberattacks were not yet common, and were not a relevant threat model.
Both C and C++ allow programmers to have full control over how they manage their apps' memory pointers (addresses), and don't come with restrictions or warnings to prevent or alert developers when they're making basic memory management mistakes.
These early coding errors result in memory management vulnerabilities being introduced in applications.
And due to the fact that many products from Google and Microsoft are using C and C++, memory safety issues became even more prevalent.
One example on how to address this issue, is what Mozilla is doing.

The Firefox-maker has been the one of a few who made a breakthrough by sponsoring, promoting and adopting the Rust programming language.
Rust is a multi-paradigm programming language that is focused on performance and safety, especially safe concurrency. Despite it is syntactically similar to C++, Rust provides memory safety without using garbage collection.
For this reason, Rust is considered one of the safest programming languages, and an ideal replacement for C and C++, primarily due to Mozilla's early efforts.
Acknowledging that both C and C++ are outdated in the modern world of technology, Google and Microsoft are also investing in exploring the alternatives.
Google said that it plans to look into "tackling the memory unsafety problem" for Chrome. The company also plans to develop custom C++ libraries to use with Chrome's codebase, which should give better protections against memory-related bugs.
The browser maker is also exploring the MiraclePtr Project, which aims to turn "exploitable use-after-free bugs into non-security crashes with acceptable performance, memory, binary size and minimal stability impact."
Google also said that it plans to explore using "safe" languages, where possible. Candidates include Rust, Swift, JavaScript, Kotlin, and Java.
As for Microsoft, the company has experimented with the Checked C project, as well as Rust, and also building its own Rust-like "safe" programming language.