China is known to track its citizens' whereabouts using cameras installed in many places in its cities.
The initiative also uses facial recognition to automatically identity the people captured on the cameras for easy and quick identification, allowing the authorities to search for practically anyone.
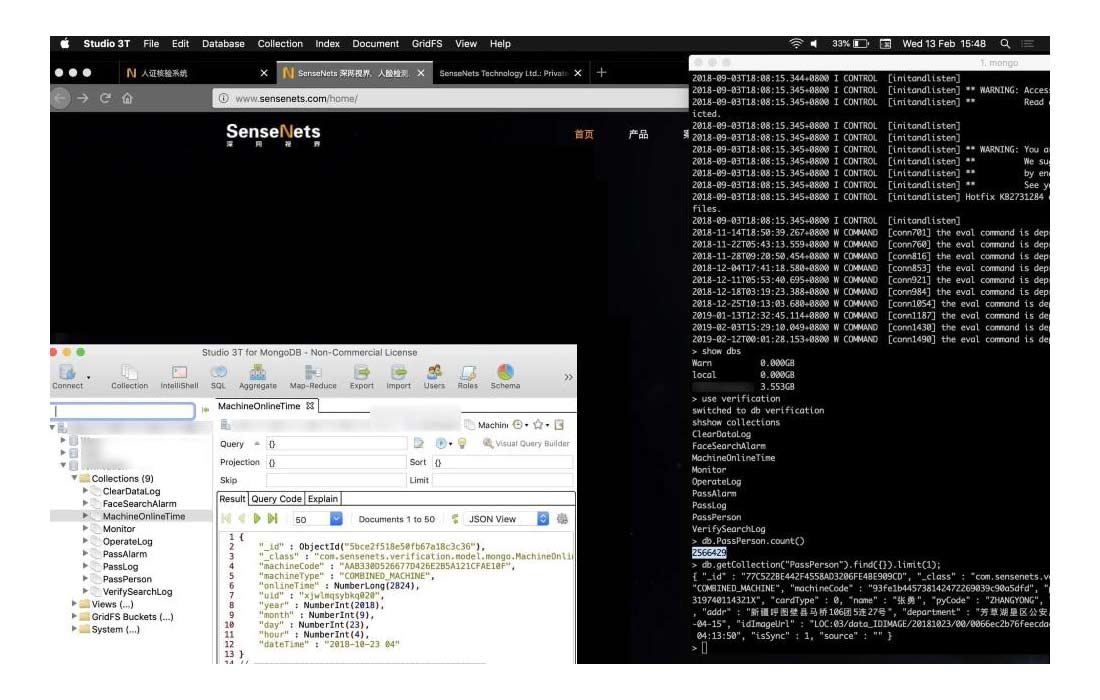
Here, one of the facial recognition databases that the Chinese government is using to track the 2.5 million population in the Xinjiang region, has been inadvertently left open on the internet for months, according to a Dutch security researcher.
The database is maintained by SenseNets, a Shenzhen-based company which provides video-based crowd analysis and facial recognition technology.
Victor Gevers who has previously found exposed MongoDB databases, found this SenseNets' MongoDB databases left exposed online without authentication.
"Knowing when someone is not in the office or at home can be useful for simple burglar crimes, but also social engineering attacks to get into buildings," Gevers said.
The database also contains highly detailed and sensitive information, including people's full name, home address, age, sex, nationality, dates of birth, photos, employer and others. There are also other information usually found on ID cards, said Gevers. This include ID card numbers, ID card issue date, and ID card expiration date.
For each user in the database, there was also a list of GPS coordinates, as well as the locations where that user had been seen.
These GPS coordinates were collected by a list of 1,039 unique "trackers", or locations of public cameras from where video had been captured and was being analyzed.
Some of the descriptive names associated with these "trackers" contained terms such as "mosque," "hotel," "police station," "internet cafe," "restaurant," and other public places where surveillance cameras can normally be found.
According to Gevers, the coordinates were all located in China's Xinjiang province, the home of China's Uyghur Muslim minority population.
What makes things worse is that, the database was exposed with full access - meaning a malicious actor could simply add or delete records from the database.
Previously, there are reports of human rights abuses carried out by Chinese authorities in Xinjiang, including forcing Uyghur Muslims in to install a specially-made spyware on their phones, or forcing the Muslims into "re-education" camps considered by many as forced labor camps.
The database that Gevers found wasn't old, as in the 24 hours of his analysis, he saw a stream of nearly 6.7 million GPS coordinates actively recording. What this means, the database was still tracking Uyghur Muslims as they moved.
Gevers reported the exposed database to SenseNets, which secured it by blocking access from non-Chinese IP addresses using a firewall.
SenseNets that was founded in 2015, is a government contractor, helping the authorities to track the Muslim minority. This is the reason why SenseNets has access to such detailed information, as well as the camera feeds from police stations and other government buildings.
China's surveillance technology has often been criticized as an invasion of privacy, mostly by the west, as it allows the government to track citizens in real-time without their consent.