Routers are networking devices that forward data packets between computer networks. In other words, they are the devices that perform the traffic directing functions on the internet, allowing connected devices to browse the web.
Most of thethese devices are plugged in and undergone setup just once in their lifetime. Users tend to forget about the presence of these devices, up until the internet stops working for them.
Routers are simply the gateway to the internet, and researchers at Germany's Fraunhofer Institute for Communication, Information Processing and Ergonomics (FKIE) found that they are riddled with flaws due to manufacturers neglecting the security of the devices.
Making things worse, some of the flaws are alarming.
"Our results are alarming," the researchers at Germany's Fraunhofer Institute write in a report pointing to security holes in common internet routers for private users.
On a Fraunhofer Institute's web page, the researchers said that:
The team tested popular models from Asus, AVM, D-Link, Linksys, NETGEAR, TP-Link and Zyxel.
Not a single router among the devices examined from those brands was without faults.
AVM, a German router manufacturer, was the only vendor that didn't publish private cryptographic keys in its router firmware. The researchers noted that AVM performed better than others in most areas, while Asus and NETGEAR did well in some other areas.
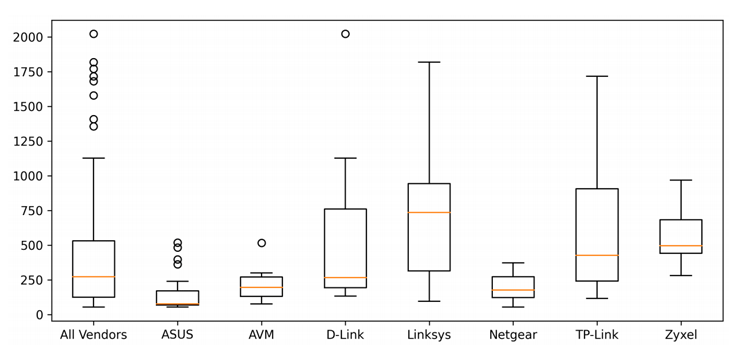
From hundreds of long-known vulnerabilities, 46 of the tested routers have not received a single security update in the last twelve months.
In the worst of the devices FKIE assessed, one Linksys router model hadn't been updated for more than five years.
"The oldest kernel version was found in the Linksys WRT54GL which is powered by a 2.4.20 Linux Kernel released in 2002," the report reads.
90% of the routers use the free operating system Linux, but often in very old versions.
Linux is known for its ability to quickly close security flaws. But unfortunately, manufacturers of the routers have neglected the frequent software updates, making their products literally vulnerable to hacks.
"Linux works continuously to close security vulnerabilities in its operating system and to develop new functionalities. Really, all the manufacturers would have to do is install the latest software, but they do not integrate it to the extent that they could and should," explained Johannes vom Dorp, a scientist at FKIE's Cyber Analysis & Defense department.
"Most of the devices are powered by Linux and security patches for Linux kernel and other open-source software are released several times a year. This means the vendors could distribute security patches to their devices far more often, but they do not."
And again making things worse, some of the manufacturers that do ship firmware updates, didn't fix known vulnerabilities. What this means, even if a consumer installs the latest firmware from the manufacturer, the router would still be vulnerable.
"Numerous routers have passwords that are either well known or simple to crack – or else they have hard-coded credentials that users cannot change," he added.
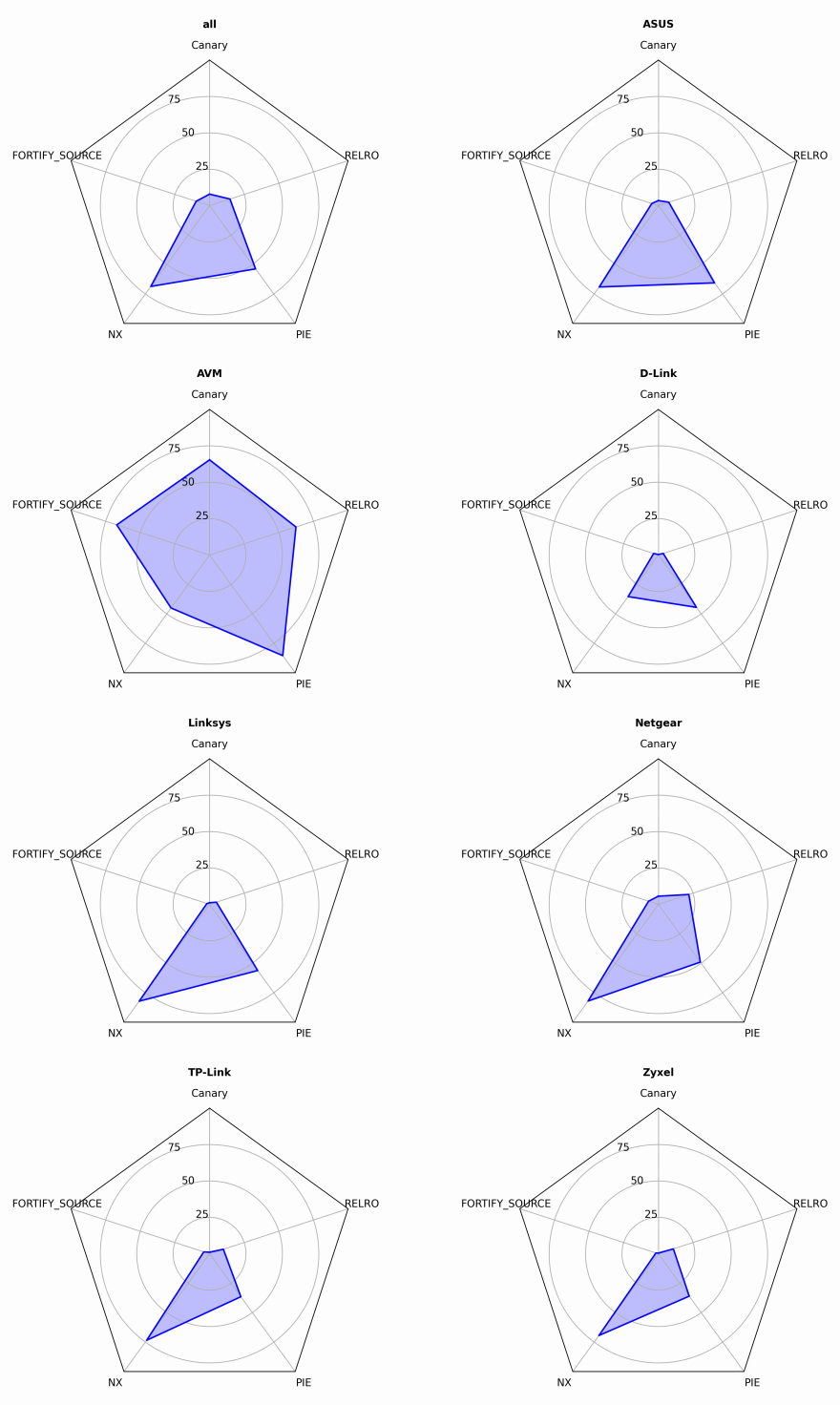
The study that was led by Peter Weidenbach and Johannes vom Dorp in the Fraunhofer FKIE’s Cyber Analysis & Defense department, targeted five key signals in firmware images to assess each manufacturer's approach to cybersecurity. They include:
- Days Since Last Firmware Update Release. Does the vendor maintain all of their products regularly? Or in other words, how often do they fix issues?
- Operating System. How old are the OS versions powering the devices? How many well-known critical vulnerabilities do these versions provide?
- Exploit Mitigation. Do the vendors activate exploit mitigation techniques?
- Private Cryptographic Key Material. Do they publish keys that should stay private for security reasons?
- Hard-coded Login Credentials. Are there any hard-coded credentials that might allow unintended access to the device?
After running and testing the 127 routers, the researchers were able to detect and identify the flaws using the Fraunhofer FKIE's Firmware Analysis and Comparison Tool (FACT).
FKIE concluded that router manufacturers are significantly lagging in the delivery of security updates compared with operating system makers.
"The update policy of router vendors is far behind the standards as we know it from desktop or server operating systems," noted FKIE.