Fraudsters are everywhere. They can use many ways to conceal their criminal activities, including altering or deleting information, changing electronic or paper documents, and creating fraudulent files.
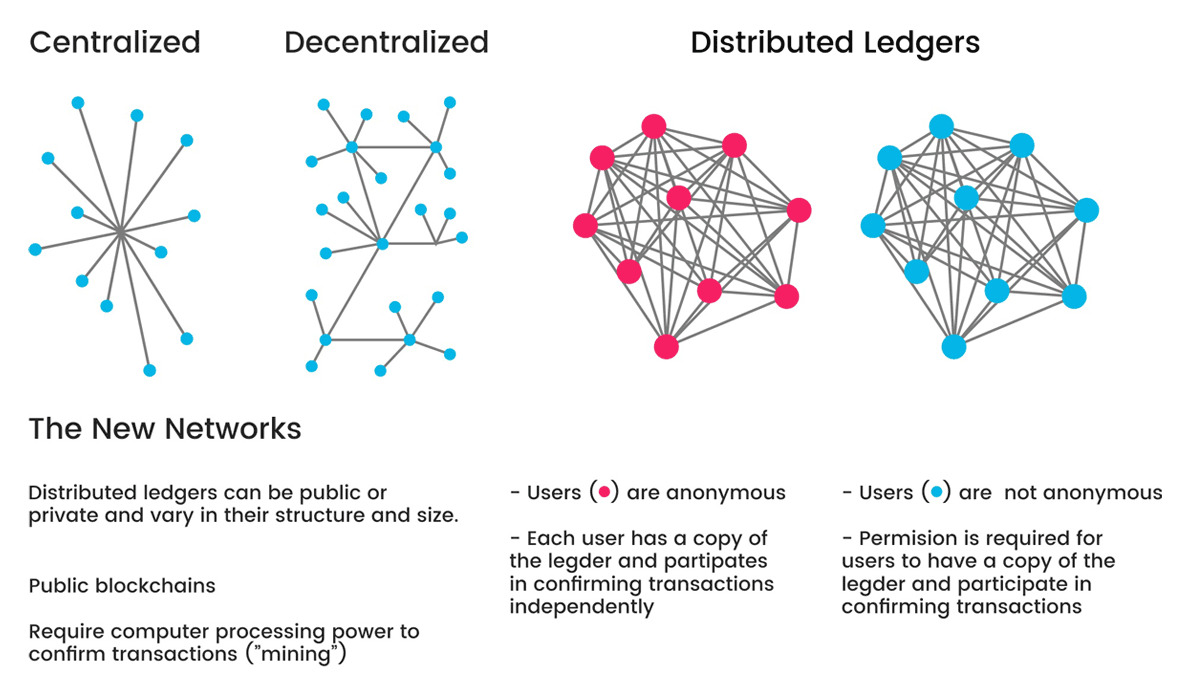
These can happen because ordinary methods of security are centralized and not transparent.
One workaround, is using a shared ledger, where trust is distributed.
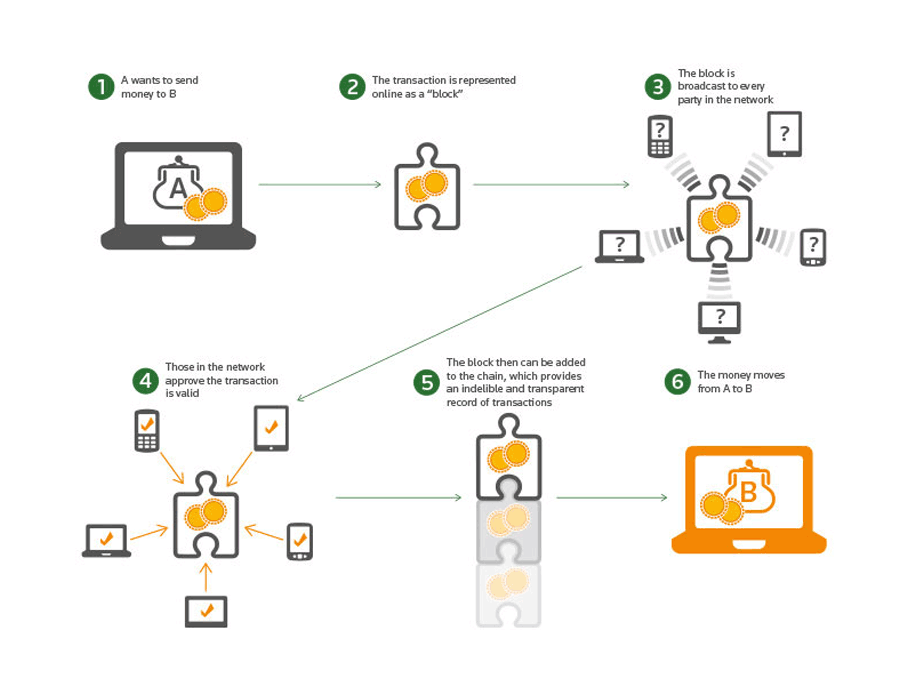
Blockchain technology is a digitized encryption method to confirm transactions. Using distributed digital ledgers, it increases the visibility and transparency of transactions made throughout a supply chain and between members of a network. What's more, the data is continuously reconciled.
Because participants can see the history and transfer of assets, fraudulent transactions are easier to identify.
Boasting of an iron-clad defense system that supposedly couldn't be hacked, blockchain also requires transactions that are going to be recorded to pass proper verification before being added.
This makes false operations even easier to detect.
And because it is decentralized, blockchain has no central administrator, meaning that management and authorization is spread across the network. This way, there should be no single point of failure present.
Blockchain Is Immutable
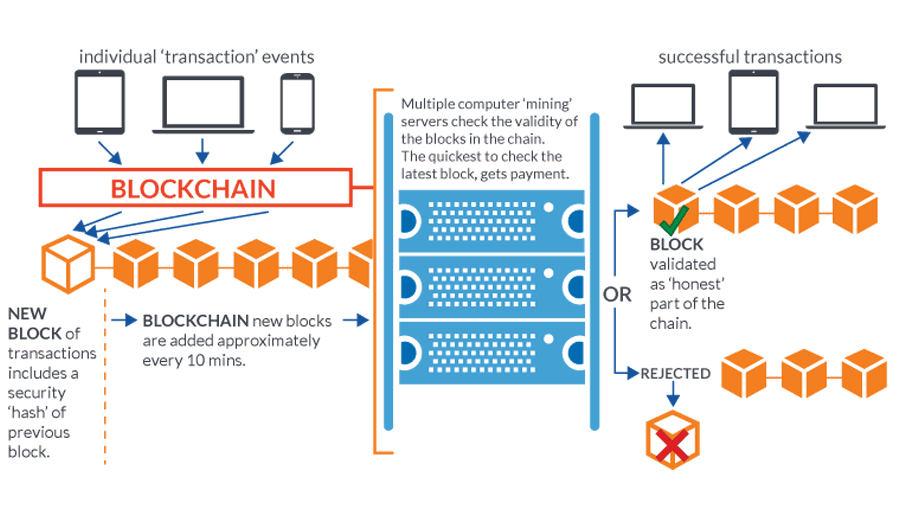
Blockchain requires transactions to be recorded to pass verification. And after that, they are immutable because they cannot be deleted or changed.
Before a 'block' of transactions can be appended to the blockchain, participants in the network must agree that the transaction is valid. This process is called consensus. When that is done, the block is given a timestamp, secured through cryptography, and then linked to the previous block in the chain.
While participants can actually create a new transaction to change the state of an asset, meaning that the new transaction will simply be added to the chain, but because data is immutable once recorded, the original data will still be accessible and transparent.
What this means, by using blockchain, people can see the provenance of an asset, including where it came from, where it has been, and who has had ownership of it.
Blockchain With Smart Contracts
In ordinary transactions, parties need to send proof, and more proof about something. This is to ensure that all parties agree and understand what's what, what is going on, and where things are coming from.
With blockchain, transactions can use what are called 'smart contracts'. This can combat fraud simply because they allow both the buyer and the seller to create "if/then" contracts, in which one step of the process won't be fulfilled until the one before is verified as completed.
Smart contracts can also remove the needs for a physical mediator.
Blockchain Can Be Permissioned
Businesses can hold and deal with a lot of confidential data.
Because that kind of data shouldn't be made public, there must be some way to prevent outsiders to get into the network and corrupt the records. In blockchain technology, this is where permissions come into play.
While blockchain in general is 'permissionless', blockchain networks can also be made 'permissioned'.
In permissionless network, anyone can join the network, participate in the process of block verification to create consensus and also create smart contracts. Anyone can become part of this blockchain network and contribute to its upkeep. In a permissioned network on the other hand, the model restricts the actors who can contribute to the consensus of the system state.
Permissioned networks can be a great way for fraud prevention because they restrict who is allowed to participate and in what capacity.
To further ensure the security, members of a permissioned network must first be invited and validated before they can contribute.
This way, companies can level up the playing ground in the modern days of digital environment by empowering users to determine what personal data and information they share, where, and with whom. This, again, can prevent fraud.
Read: The Differences Between 'Permissioned' And 'Permissionless' Blockchain
Blockchain For A Smarter And Tighter Supply Chain
In the modern days of global economy, companies all over the world partner with other companies for various needs. Some require the help of others in manufacturing, agriculture, development, and everything in between.
The problem here is that, companies can work in different ways. And because there are the distance and the barrier between them, it can be difficult to ensure that the products and processes that were agreed upon are actually followed when the final product is made.
With blockchain, companies can combat fraud by verifying the legitimacy of every part of the supply chain process, helping both the buyer and manufacturer.
Carrefour for example. The French supermarket giant became Europe's first company to put food inside a blockchain. What it does, is allowing customers to access detailed information about the origin of the product they’re buying by simply scanning a QR code on the packaging.
Blockchain Against Fraud
Since people started to understand the concept and the way blockchain works, the technology emerged as something numerous industries started adopting to store and transfer chunks of data.
Blockchain may ensure transparency and make things safer. But despite its numerous advantages, the technology has its own unique limitations when it comes to fraud prevention.
For example, the technology cannot determine the motivation behind a payment, or how a deserving recipient of a payment is really for what payment that should be being made.
One of the most famous cases, was Silk Road of the dark web, when its owner, Ross Ulbricht was convicted of money laundering, computer hacking and conspiracy to traffic narcotics using Bitcoin and Tor in an effort to evade law enforcement.
Ulbricht's Silk Road was a criminal enterprise which allowed the sale and purchase of illicit goods, such as false passports, guns and drugs. It was Silk Road in using blockchain that made it possible for the authorities to uncover corruption.
Without blockchain, it would have been extremely difficult for them to trace the corruption, simply because the blockchain cryptography means that records cannot be traced or tampered with. This led to an asset tracing exercise and the movement of funds could be followed after they had gone into one person or company, to another.
The case was a clear example of how the blockchain method can prevent fraud and corruption, but not preventing the initial wrongdoing.
Another weakness in blockchain, is the 51% attack.
Mining is a complex, expensive process responsible for maintaining the integrity of the technology. Blockchain miners are responsible in adding new 'blocks' of transactions to the chain, confirming that each part of the transaction is valid. In turn, they are rewarded in cryptocurrency.
This mining process is complex, and requires a high amount of computing power.
However, if a miner or group of miners were to hypothetically gain more than 50% of the computing network, they can control and manipulate the chain. For example, they can add new transactions to the chain without spending.
One example of this case, happened back in May 2018, when the Bitcoin Gold blockchain was attacked by a set of coordinated actions. A total of $70,000 in Bitcoin Gold (BTG) was double-spent. As a result, BTG was delisted from Bittrex.
This happened because an individual or group of individuals in collusion have to control a majority of the system to tamper with the transaction records on a blockchain. This condition however, is more difficult to accomplish than tampering itself.
Other examples include:
- Phishing where fraudsters send out emails that mimic legitimate emails from reputable companies. Some of the phishing scams use the victims' computer as a host for illegal cryptocurrency mining.
- Sybil attacks, which involve malicious authors in creating multiple false identities on a peer-to-peer network. Because blockchain networks run various nodes at the same time, swarming a network with false identities can cause the system to crash.
- Blockchain technology relies on the upload and download of large volumes of information in real time. This makes it vulnerable to routing attack, where hackers intercept data that is transferred to internet service providers. This way, the system is partitioned but appears to be functioning as usual.
Blockchain should be welcomed because it can prevent fraud with its deterrent effect in some business sectors and in some parts of individual businesses. It may also be the best development in financial services security.
But despite its numerous advantages, it will never deter or prevent all kind of frauds.
.
Faud is not limited to actors leveraging methods and strategies to trick others to benefit their own, because fraud is evolving in response to changing circumstances and conditions.
Therefore, businesses need to still take it upon themselves to prevent fraud.
Some of the ways, include:
- Two-factor authentication: Also called two-step verification or 2FA, the term has become familiar in blockchain technology. 2FA adds a layer of security to wallets where users not only provide the wallet key but also provide a one-time password, or OTP, generated in real time to access the currency wallet. This way, if ever fraudsters maliciously gain access to users' password, they would have to own the pre-set OTP device to access the wallet.
- Anti-phishing software: Designed specially to identify malicious links, email threats, fake websites and revoke access, anti-phishing software in many cases can also approve legitimate websites and links. What this means, the security solutions can protect users from malicious attack campaigns that have been used on a mass scale, or from both familiar and unknown forms of phishing threats.
- Cold wallets: There are typically two types of wallets in cryptocurrency: a hot wallet which is connected to the internet, and a cold wallet which isn't. Cold wallets are much more secure because they are less vulnerable to hacking.
- Blacklisting: By identifying fraudulent initial coin offerings, phishing patterns and key/identity thieves and blacklisting them, companies can protect themselves from falling victim to repeated patterns of fraud.
Further reading: How Blockchain Technology Can Change The Way Modern Businesses Work