
In April 3rd, 2020, the novel 'COVID-19' coronavirus has infected more than 1 million people. The rising number has left many others living in fear of the pandemic.
Many malicious actors have spread spam emails by using topics like secrets to the virus, remedy cures and others, to appeal potential victims.
Among the many ways, malicious actors have piggybacked the trend to distribute malware, by using a fake coronavirus map, fake coronavirus tracker, and lot more.
This time, those actors go beyond that by making use of a once dormant malware.
The malware is called the 'Zeus Sphinx', and it has been absent from the digital threat landscape for about three years, until the coronavirus pandemic resurrected it.
Hackers started to use this malware in order to capitalize on the trend.
The malware that is also known as Zloader or Terdot , was first detected in the wild back in August 2015.
It emerged as a commercial modular banking Trojan with its codes sharing elements from the ieaked infamous Zeus v2 banking Trojan.
Like other banking Trojans, Zeus Sphinx’s core capability is to harvest online account credentials for online banking sites (and some other services). It does this by waiting for infected victims to land on a targeted online banking portal.
When this happens, the malware will dynamically fetch web injections from its command-and-control (C2) server to modify the page that the user sees, so that the information that the user enters into the login fields is sent to the cybercriminals.
It began to carve its name to fame when it targeted financial institutions across the U.S., UK, Australia and Brazil.
According to researchers Amir Gandler and Limor Kessem at IBM X-Force, the malware began resurfacing in December 2019.
However, the researchers observed a significant increase in volume in March, as Sphinx’s operators looked to take advantage of the interest and news around government relief payments for the COVID-19.
According to the researchers in a website post:
"Once the end user accepts and enables these malicious macros, the script will start its deployment, often using legitimate, hijacked Windows processes that will fetch a malware downloader. Next, the downloader will communicate with a remote command-and-control (C2) server and fetch the relevant malware — in this case, the new Sphinx variant."
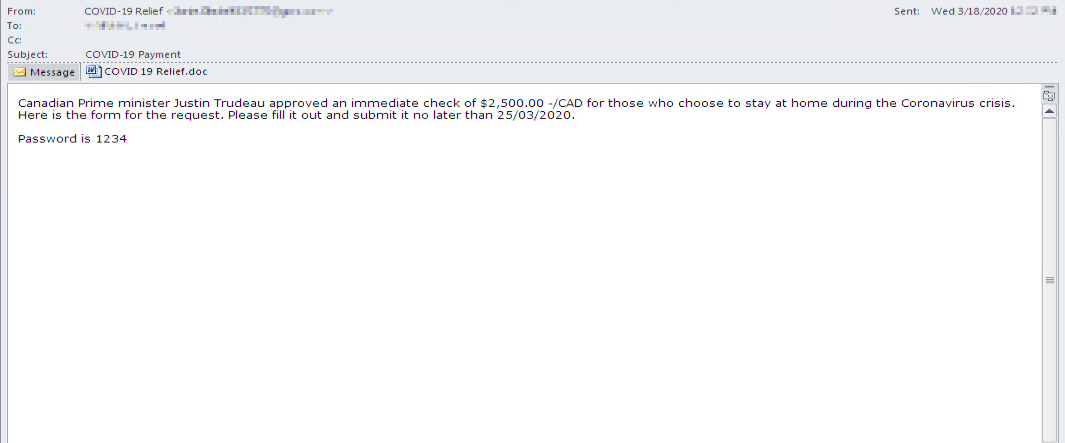
The researchers said that the Zeus Sphinx is being spread through phishing campaigns loaded with malicious files named "COVID 19 relief."
The malicious actors crafted specialized emails to tell victims that they need to fill out an attached form to receive monetary compensation for having to stay at home to help fight increasing infection rates.
Once installed on a compromised machine, Zeus Sphinx maintains persistence by dynamically writing itself to numerous files and folders, as well as creating multiple registry keys.
The malware also attempts to avoid detection as malicious software by using a self-signed certificate.
Fortunately, the techniques Zeus Sphinx use are similar to Zeus v2, and inherits one of its flaw, which is inability to reinstall itself when victims update their browser.
The return of Zeus Sphinx simply adds the growing fray of COVID-19-themed phishing and malware-spam campaigns that happen worldwide.